Feeling secure, isn’t a Moonshot.
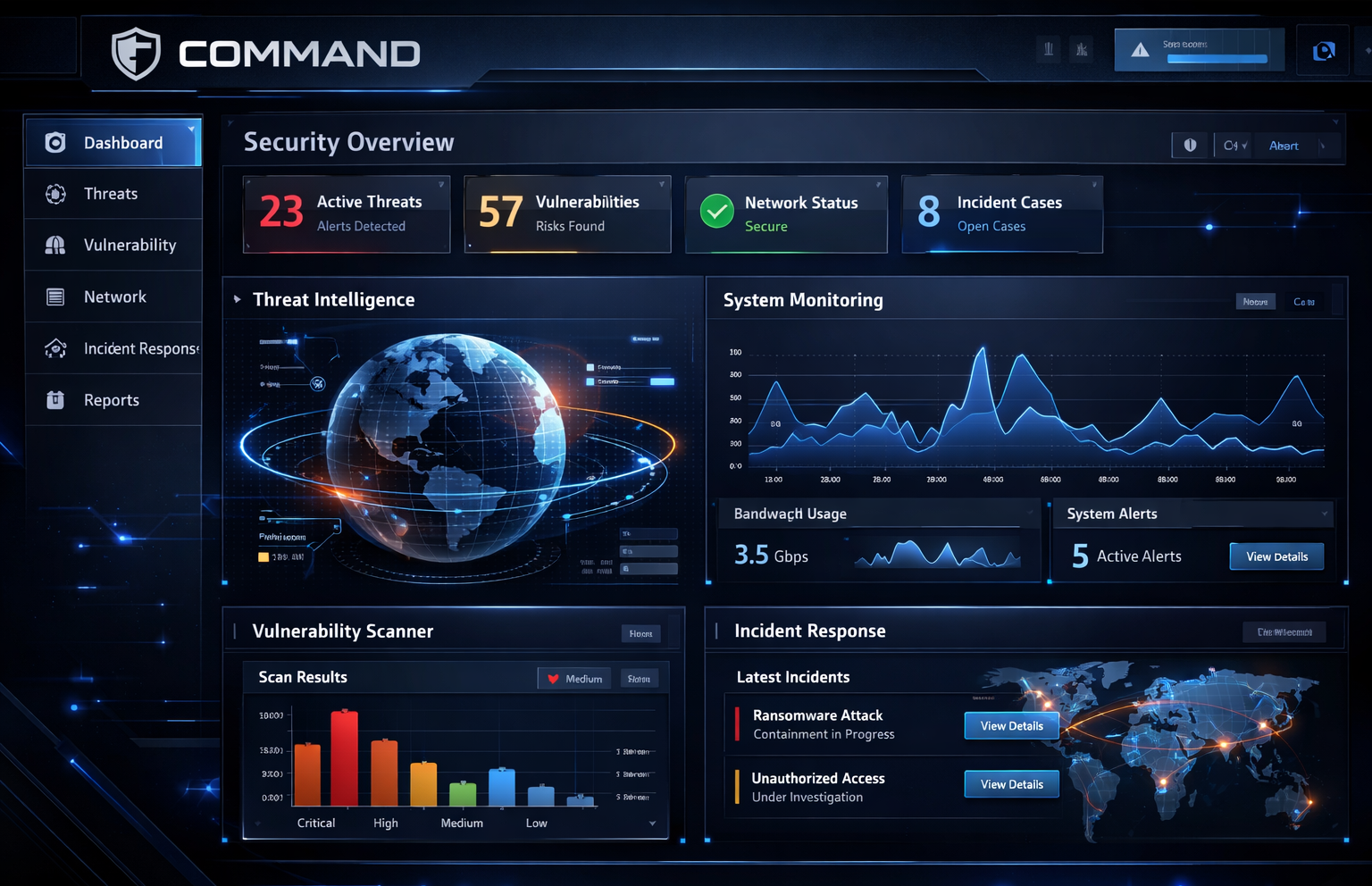
TOTO-L COMMAND™ is our integrated Zero Trust cybersecurity platform built in partnership with the team at Moonshot LLC, designed to protect complex IT, OT, ICS, and cyber-physical environments where traditional perimeter defenses and static security controls are insufficient.
TOTO-L COMMAND™ operationalizes Zero Trust by closing the loop between authoritative discovery, intelligent decision-making, and real-time defense, enabling continuous verification, least-privilege access, and adaptive enforcement aligned with CISA Zero Trust guidance and DoD Cyber Protect objectives. The platform is composed of: CMD-DISCOVER™ , CMD-DECIDE™ , and CMD-DEFEND™ .
Together, these capabilities provide government and industry operators with a scalable, system-agnostic Zero Trust capability that evolves with the network, minimizes operational burden, and ensures resilient security across high-consequence environments.
-
CMD-DISCOVER™ is a foundational cyber capability designed to establish an authoritative, continuously validated map of a user’s network down to the physical sensor and process level.
CMD-DISCOVER™ identifies, inventories, and accounts for every device, controller, actuator, and sensor operating on the network, providing operators with a ground-truth understanding of what is connected, where it resides, how it behaves, and whether it can be trusted. Purpose-built for OT, ICS, and cyber-physical environments, CMD-DISCOVER™ closes long-standing visibility gaps that leave organizations unable to fully account for undocumented, misconfigured, or manipulated equipment at the lowest layers of the Purdue Reference Model.
By continuously validating device identity and behavior at Layer 0 and Layer 2, CMD-DISCOVER™ enables precise asset accountability and early detection of malfunction, spoofing, or unauthorized activity at the source. Delivered as a software-only solution compatible with both legacy and modern infrastructure, CMD-DISCOVER™ provides the trusted data foundation required for Zero Trust architectures and advanced automation.
-
CMD-DECIDE™ is an advanced cyber intelligence capability that applies AI and machine learning to autonomously develop, enforce, and continuously refine policy-based access controls across complex environments.
Observing network behavior, asset relationships, and operational context is how CMD-DECIDE™ learns how systems are intended to function, then translates that understanding into adaptive, explainable security policy with minimal human intervention.
As networks and mission conditions evolve, CMD-DECIDE™ continuously updates access decisions based on observed behavior, risk posture, and operational requirements. This enables dynamic least-privilege enforcement, rapid accommodation of new devices and workflows, and automated correction of policy drift—without disrupting operations.
By replacing static rules with continuously informed decisions, CMD-DECIDE™ significantly reduces operational burden while maintaining strict alignment with Zero Trust principles.
-
CMD-DEFEND™ is the enforcement and control plane of the COMMAND platform, translating Zero Trust principles into real-time, mission-aligned defense. Leveraging authoritative asset discovery from CMD-DISCOVER™ and AI-driven policy decisions from CMD-DECIDE™, CMD-DEFEND™ dynamically enforces least-privilege access, microsegmentation, and continuous authorization across IT, OT, ICS, and cyber-physical environments.
Designed for minimal footprint and latency, CMD-DEFEND™ integrates seamlessly with legacy and modern infrastructures and adapts to changing mission conditions without manual reconfiguration. This enables resilient, system-agnostic enforcement aligned with the CISA Zero Trust Maturity Model and DoD Cyber Protect objectives, even in contested or high-consequence operational environments.
Let’s Work Together
If you're interested in working with us, complete the form with a few details about your project. We'll review your message and get back to you within 48 hours.